“YOU builds the future, FORTIFY makes it secure"
External Network Penetration Testing Methodology
External Network Penetration Testing simulates real-world cyberattacks against your public-facing systems to identify vulnerabilities before malicious actors exploit them. At Fortify Solutions, we follow an industry-standard approach based on the Open Source Security Testing Methodology Manual (OSSTMM), enhanced with our proven in-house practices.
PENETRATION TESTING
Fortify Solutions
8/1/20251 min read
External Network Penetration Testing Methodology
Overview
External Network Penetration Testing simulates real-world cyberattacks against your public-facing systems to identify vulnerabilities before malicious actors exploit them.
At Fortify Solutions, we follow an industry-standard approach based on the Open Source Security Testing Methodology Manual (OSSTMM), enhanced with our proven in-house practices.
Our goal: Expose security gaps, validate your defenses, and provide clear remediation guidance—all while ensuring zero disruption to your business operations.
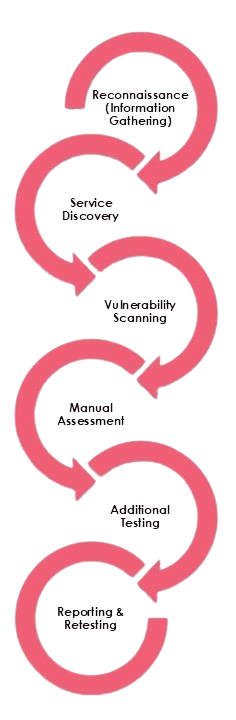
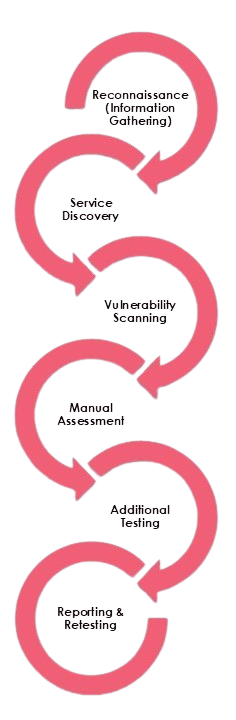
Our Testing Process
Reconnaissance (Information Gathering)
Identify what’s publicly visible about your organization: domains, subdomains, IP addresses, exposed services, email configurations, employee details, and leaked credentials.
Sources include corporate websites, public databases, WHOIS records, search engines, and dark web repositories.
Tools: Nmap, Shodan, Censys, DirBuster.
Service Discovery
Detect open ports, running services, and exposed applications on your internet-facing systems.
Map service versions, operating systems, and potential misconfigurations.
Tools: Nmap, Aquatone, EyeWitness, testssl.sh.
Vulnerability Scanning
Identify security flaws in exposed services—unpatched software, weak encryption, default credentials, and misconfigurations.
Evaluate risks such as data leakage, service disruption, website defacement, and domain blacklisting.
Tools: Nessus, Burp Suite, Nikto, Metasploit.
Manual Assessment
Validate and safely exploit vulnerabilities to measure real-world impact.
Examine high-value targets such as:
Web & email servers
DNS, firewalls, and routers
Office 365 instances
VPN endpoints and remote access services
Special focus: Outdated software, insecure legacy protocols, and weak authentication.
Tools: Burp Suite, sqlmap, Postman, Metasploit.
Additional Testing (as per scope)
Custom exploitation scripts
Public exploit frameworks
Manual configuration reviews
Reporting & Retesting
Deliver a detailed, risk-prioritized report with:
Step-by-step remediation guidance
Security posture improvement recommendations
Retest remediated issues to ensure vulnerabilities are fully closed.
Why This Matters
A single overlooked vulnerability in your external network can lead to:
Data breaches and leaks of sensitive corporate information
Financial and reputational loss
Service downtime affecting customers and operations
Exploitation of your infrastructure for further attacks
Our testing ensures you see your network the way attackers do—so you can secure it before they try.
© 2025. All rights reserved.


Fortify Solutions
Empowering organizations through expert cybersecurity solutions.
GSTIN - 27CERPD1763G1ZD
UDYAM REG. No. UDYAM-MH-33-0151333
CONTACT US
+91 9823449055
business@fortifysolutions.in
sales@fortifysolutions.in
